Forecasting the Cyber Threat Landscape: What to Expect in 2025

2024 marked a pivotal shift in the cyber threat landscape, with threat actors increasingly experimental, yet intentional in their approaches to cyberattacks. Leveraging new and emerging technologies to weaponise trust and further lower the barrier to entry for cybercriminals, we anticipate no less for 2025. Based on PwC Dark Lab’s observations throughout 2024, we share our assessment of the potentially most prevalent threats and likely emerging trends for this year.
Identities will continue to be the primary target for threat actors, resulting in a gradual rise of infostealer infections and credential sales on the dark web
Hong Kong saw a 23% rise in infostealer infections in 2024, further reflected in our incident experience, as infostealers and leaked credentials persisted as a frequent root cause in cyberattacks. We assess this growth in infostealer usage is given the wider trend observed, whereby threat actors of varying motivations have increasingly shifted focus to identity-based attacks.

Through our ongoing dark web monitoring, we observed threat actors have become increasingly deliberate in their weaponisation of infostealers – intentionally targeting specific types of data during collection. This is as reflected in the uptick of network access sales for SSH, VPN, firewall, and cloud. We posit that credentials and database sales will remain a hot commodity within the dark web marketplaces given they allow for easy entry. Furthermore, we observed that data sales are not always need to be associated with an active data breach – as we repeatedly observe threat actors farming data from organisations’ exposed libraries, directories, publicly released information, as well as historically leaked data on the dark web – to publish as a single data dump on the dark web. We posit this repurposing and collating of already available information is performed by threat actors as a means to establish their reputation on dark web hacking forums.
As witnessed in our incident experience and open-source reporting, threat actors now target individuals’ personal devices with the intention to obtain access to enterprise environments. Thiswas most recently evidenced Cyberhaven’s Chrome extension security incident, whereby a phishing attack resulted in attacker takeover of their legitimate browser extension. Replacing the extension with a tampered, maliciously-embedded update designed to steal cookies and authenticated sessions, the extension was automatically dispensed to approximately 400,000 users.[1] In a previous incident, we observed that the victim organisation was compromised as a result of an infostealer deployed on their employee’s personal, unmanaged laptop, leading to the obtaining of valid corporate credentials and subsequent corporate compromise. We anticipate that threat actors will continue to adopt new means to distribute and weaponise infostealers at mass to collect valid identities to initiate their attacks.
Cybercriminals will exploit any means to deliver malware, with Search Engine Optimisation (SEO) being a good mode for compromise – bringing potential reputational damage
Search Engine Optimisation (SEO) plays a crucial role in today’s digital society, enabling visibility and accessibility of websites to seamlessly connect users with the most relevant information. As such, it’s no surprise that SEO has become a growing driver in malicious campaigns. Be it directing users to malicious sites impersonating legitimate brands, spreading of disinformation, or compromising legitimate websites to benefit from their SEO results, threat actors have continuously refined their means to weaponise, or ‘poison’, SEO.
SEO poisoning involves the manipulation of search engine results to direct users to harmful websites. This may be achieved via the use of popular search terms and keywords to increase their sites’ ranks, mimicking of legitimate websites, typosquatting, and/or leveraging cloaking and multiple redirection techniques. Recently, we observed public reports regarding the distribution of a novel multipurpose malware, PLAYFULGHOST, distributed as a trojanised version of trusted VPN applications via SEO poisoning techniques.[2] In other cases, we observe threat actors installing ‘SEO malware’ on compromised websites – designed to perform black hat SEO poisoning, whereby search engines display the attackers’ malicious webpages as though they were contained within the legitimate, compromised website.[3]
In mid-2024, PwC’s Dark Lab have observed a sharp uptick in phishing sites masquerading as online gambling operators. Targeted against users in Southeast Asia, we assessed this is likely due to regional crackdown on online gambling – as evidenced in Philippines’ ban of Philippine Offshore Gaming Operators (POGOs). A notable instigator for the ban on POGOs was the shift into illicit scamming activities by POGOs following the impact of COVID-19 (e.g., online fake shopping, cryptocurrency, and investment scams).[4] As we observe further crackdowns within the region, we anticipate a growth in SEO campaigns pushing online gambling phishing sites, preying on unsuspecting, or vulnerable users. Furthermore, this reflects on how threat actors continue to opportunistically weaponise current events to their benefit.
Growth in identity-based attacks highlights threat of domain abuse and need for stringent governance of top-level domains (TLDs)
The topic of internet hygiene has come to our attention amidst the significant uptick in the amount malicious sites impersonating local Hong Kong brands. Globally, the landscape of domain registration has become increasingly under question due to the ease and anonymity with which domains can be purchased, facilitated by the lack of regulations surrounding Know Your Customer (KYC) processes. This has fostered a favourable environment for malicious actors to disguise their infrastructure, gaining trust via ‘reputable’ top-level domains (TLDs). Whilst some TLDs like [.]xyz and [.]biz are widely regarded as ‘untrustworthy’, we observe commonly trusted TLDs [.]com and [.]top persist as the two most abused TLDs in 2024.[5]
DNS abuse can take many forms, though ICANN defines it as; botnet, malware delivery, phishing, pharming, and spam.[6] Distributed Denial of Service (DDoS) is an example of an ever-present DNS-related threat increasingly observed in 2024, with the motivations behind these attacks being hacktivist in nature and correlating with major geopolitical events (e.g., elections, ongoing tensions). We anticipate a continuation of geopolitical-motivated DDoS attacks in 2025, as threat actors recognise the success that may be achieved through these attacks; being reputational damage and heightened visibility towards their hacktivist cause. In Q2 2024, we uncovered an active campaign masquerading as multiple local brands including Mannings and Yuu using typosquatted domain names registered to [.]top, [.]shop, and [.]vip TLDs. This campaign revealed how customised attacks against individuals are becoming; targeting of personal data now spans beyond credential harvesting – further collecting a broader set of attributes such as the device you are using, user location, behaviour patterns, and even loyalty program details. As highlighted during our 2024 Hack A Day: Securing Identity, identity is now contextual – collecting various attributes or ‘unique identifiers’ to build your holistic identity-profile.
Through PwC Dark Lab’s ongoing efforts to safeguard Hong Kong citizens, we foresee a need for more structured and regular analysis of generic TLDs (gTLDs) – e.g., [.]com, [.]top and country code TLDs (ccTLDs) – e.g., [.]com.hk, [.]hk. To proactively identify and mitigate against these active threats, we anticipate that in the longer run, governance is necessary to enforce and ensure adherence on registrars. This includes intelligence-driven ongoing detection, establishing consistent definitions, uplifting KYC validations, and appropriate procedures to handle known-bad domains. With over 96% of Hong Kong’s population (aged 10 or above) using the Internet[7], it is crucial that registrars collaborate in the collective goal to secure the internet and disrupt threat actors’ infrastructure supply.
Sophistication of social engineering scams will amplify as threat actors ‘smish’, abuse legitimate services, and weaponise automation intelligence
As organisations worldwide have invested efforts into hardening their security posture, we observe threat actors adapting their attacks to find alternative means to bypass the heightened defences. SMS phishing (“smishing”) has become increasingly tailored in response to heightened user awareness. In some cases, we have observed smishing messages no longer containing links, only phone numbers – suggesting a preference to perform voice call phishing (“vishing”) as a means of increasing their chances of success. Beyond abuse of trusted identities, we observe threat actors weaponising legitimate services to disguise their malicious traffic behind legitimate sources.
In Q4 2024, we observed an unknown threat actor leverage multiple trusted domains in Hong Kong to front their Cobalt Strike Beacon C2. Domain fronting is a technique used to disguise the true destination of Internet traffic by using different domain names in different layers of an HTTPS connection to route traffic through a legitimate and highly trusted domain. Similarly, we have observed the use of legitimate platforms such as Ticketmaster and Cloudflare to host phishing sites. In another context, our global counterparts have observed advanced persistent threat (APT) actors utilising TryCloudflare tunnels to stage malware and circumvent DNS filtering solutions. We project that threat actors will continue to experiment with different, legitimate platforms to find means to facilitate their attacks.
As observed since the emergence of ChatGPT in late 2022, generative artificial intelligence (AI) has enabled threat actors to craft highly convincing, tailored social engineering contents at scale. This was observed in 2024, as the U.S. Federal Bureau of Investigation (FBI) observed a surge in AI-driven financial fraud, leveraging GenAI to generate convincing phishing emails, social engineering scripts, and deepfake audio and video to deceive victims.[8] We predict that the application of AI by cybercriminals will expand beyond content generation to automate vulnerability exploitation, malware distribution and development, and AI-enabled ransomware. On the flipside, as the integration of AI into business processes rises, the need to secure these AI systems will continue to mount.
The ransomware landscape will continue to diversify, weaponising emerging technologies, trusted identities and services to increase their chances of success
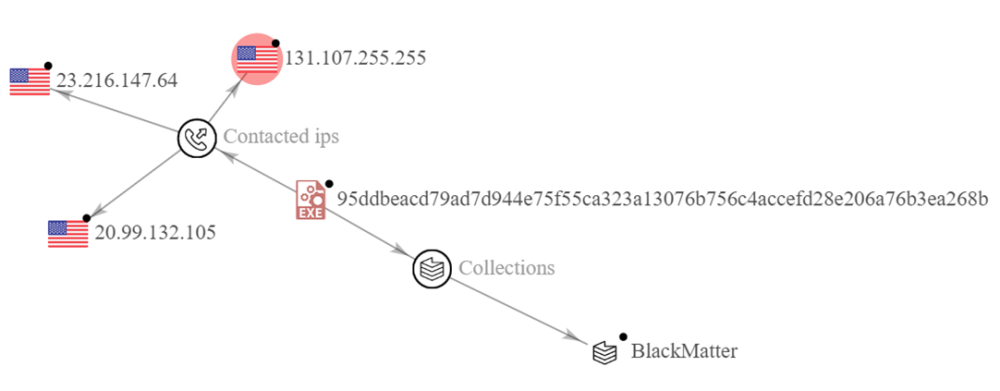
2024 was a transformative year for the ransomware landscape, following continued disruptions of the LockBit Ransomware-as-a-Service (RaaS) operations by international law enforcement agencies, and BlackCat’s alleged exit scam. These occurrences resulted in heightened scepticism, posing an opportunity for new ransomware actors to enter the market. As new groups arise, we observe them increasingly experimental in their approaches to ransomware attacks – both through the Techniques, Tactics, and Procedures (TTPs) used and their malware offerings – diversifying the threat of ransomware.
We anticipate that 2025 will see a continuation of this trend, with an increased focus on weaponising trusted identities and legitimate services to increase their chances of success. Infostealers and Initial Access Brokers (“IABs”) will likely persist as a growing infiltration vector for ransomware affiliates, as we project increased targeting against systems likely to house sensitive information to enable rapid “smash and grab” attacks, such as cloud, Software-as-a-Service (SaaS), and file transfer platforms. Target systems for ransomware encryption are expected to further expand – as we already observed in mid-2024, with threat actors increasingly developing custom strains to target macOS and Network Attached Storage (NAS). This is evidenced in the recent discovery following the arrest of a LockBit developer that the group are working on tailored variants to target Proxmox and Nutanix; virtualisation service providers.[9]
Furthermore, we have observed discussion within the cybersecurity community regarding “quantum-proof ransomware”. As quantum computing develops, we hypothesise that ransomware operators will leverage the technology to harden their encryption processes and eliminate opportunities for victims to decrypt their data without the attacker-provided decryptors. On the other hand, we observe “harvest now, decrypt later” repeatedly referenced in these discussions, as researchers anticipate threat actors will weaponise quantum computing to enable mass decryption of previously stolen information. We further suspect that this may lead to attackers collecting and storing data from recent attacks even if unable to crack in the meantime. This poses a threat to existing victims of ransomware attacks, given the potential for ransomware actors to recover highly sensitive information and repurpose their past attack to extort victims and/or sell databases on the dark web.
Recommendations to Secure Your 2025
As we enter 2025, there is no telling with certainty what threats lie ahead. However, our experiences from 2024 have provided valuable lessons on how organisations can continue to strengthen their defences against ever-evolving threats.
- Reduce your “low hanging fruit”. Monitor, minimise, and maintain visibility of your attack surface exposure to proactively identify and remediate potential security weaknesses that may expose you to external threats.
- Enforce 24×7 dark web monitoring to swiftly detect and mitigate potential threats, ensuring early detection of compromised data, i.e. leaked credentials from infostealer dumps.
- Extend 24×7 monitoring to social media listening, and brand reputation monitoring to identify mentions or impersonation attempts of your organisation, which may be indicative of potential or active targeting against your organisation.
- Adopt an offensive approach to Threat and Vulnerability Management (TVM) to achieve real-time visibility of your attack surface through autonomous, rapid detection and remediation against emerging threats.[10] This further allows for the discovery of shadow IT, which may otherwise fall under the radar and pose threats to your organisation.
- Periodically review your asset inventory, ensuring Internet-facing applications, exposed administrative ports, and non-production servers are intended to be publicly accessible, are appropriately configured, and segmented from your internal network. Ensure Internet-facing applications are regularly kept up-to-date, and prioritised in your patch management process.
- Leverage canary tokens both on the external perimeter and internal environment to detect unauthorised attempts to access your environment and/or resources. Further, leverage the canary token detection alerts to provide insight into the types of threats actively targeting your organisation and what services and/or data they seek to access.[11]
- Uplift identity security and access control. 2024 showed no signs of threat actors weaponising identities, and shed light on the importance of account housekeeping and appropriate access control provisioning.
- Govern and provision appropriate access controls and permissions following the principle of least privilege for all users. Ensure access is conditional and restricted only to the resources necessary for a user to perform their job functions. This includes enforcement of strong authentication mechanisms, such as strong password policies, multi-factor authentication (MFA), role-based access controls (RBAC), and continuous behavioural-based monitoring to detect anomalous behaviour.
- Review and uplift the process for managing credentials, particularly in the case of offboarding or unused accounts. This includes timely revocation of access (termination of account), password changes for any shared accounts the employee had access to, and ensuring the offboarded member’s MFA mechanism is no longer linked to any corporate accounts.
- Log, audit, and monitor all privileged account sessions via real-time monitoring, facilitated by Privileged Access Account (PAM) and Privileged Account and Session Management (PASM) solutions.
- Protect your “crown jewels”. As threat actors become increasingly intentional in the systems and data they target, it is crucial that organisations identity, classify, and secure the critical systems most likely to be targeted.
- Leverage threat intelligence and continuous monitoring of your attack surface (e.g., canary tokens) to identify the systems actively being targeted by threat actors.
- Prioritise systems hosting critical data (e.g., file transfer systems) with layered preventive and detective strategies to safeguard data (e.g., Data Loss Prevention (DLP)).Regularly perform risk assessments against critical systems to evaluate the current state of its cybersecurity posture, and harden accordingly.
- Regularly perform risk assessments against critical systems to evaluate the current state of its cybersecurity posture, and harden accordingly.
- Review and uplift the lifecycle of data, including considerations of;
- Where data is being shared?
- Who has access, including consideration of third-party risks posed by vendors’ access to internal data?
- What internal policies are enforced to govern staff on the handling of data? For example, no sharing of internal data via external communication channels such as WhatsApp.
- Manage your “unknown” risks. Unmanaged devices, shadow IT, and third-party risks continue to pose significant threats to organisations, introducing potential opportunities for threat actors to exploit for infiltration and/or access to your sensitive data.
- For unmanaged devices;
- Develop a Bring Your Own Device (BYOD) policy to govern the use of personal devices allowed to access the corporate network, including guidelines to enforce use of strong passwords and encryption. Regularly perform user awareness training to ensure understanding and adherence with guidelines and best practices.
- Consider implementation of a Mobile Device Management (MDM) or Endpoint Management solution to gain visibility and control over all devices connect to your network.
- Isolate unmanaged devices from critical network segments to minimise potential damage and access to resources.
- For shadow IT;
- Ensure that only authorized personnel can create and publish webpages. Use role-based access controls to limit who can make changes to corporate web assets.
- Consider use of a Content Management System (CMS) that requires approval from dedicate personnel(s) prior to webpage launch to ensure all webpages comply with security standards.
- Conduct regular audits to identify unauthorized webpages and monitor for any new web assets that appear without proper authorization. Use automated tools to scan for shadow IT activities.
- For third-party risks;
- Perform thorough due diligence to vet third-party vendors and fourth-party vendors through vendor risk management and ongoing monitoring. This includes assessment of their vulnerability management processes, security controls, and incident response capabilities.
- Implement robust vendor management program that includes regular assessments, audits, and contractual agreements that define security requirements and expectations.
- Restrict third-party access to specific network segments, enforcing the principle of least privilege alongside stringent access controls.
- For unmanaged devices;
- Counter the threat of DNS abuse. As threat actors increasingly abuse DNS infrastructure to enhance the capabilities of their attacks, it is crucial that organisations and registrars maintain awareness of the latest threats.
- For individuals and organisations; maintain awareness of the threat of DNS abuse, including visibility of which registrars should be perceived as higher-risk, and continuous tracking of DNS-related threats.
- For registrars, we recommend reviewing and uplifting the Know Your Customer (KYC) process, and establishing continuous monitoring to proactively flag DNS abuse. Monitoring would cover DNS/WHOIS data, combined with community reports of suspicious domains (e.g., via VirusTotal, URLScan, etc.).
- For ICANN, we recommend to lead the industry; establish and enforce the governance and security key risk indicators (KRIs) on whether registrars are in compliance; what are the penalties; what are the trends of threat actors, and how the registrars and organisations should detect, respond, and recover.
Feel free to contact us at [darklab dot cti at hk dot pwc dot com] for any further information.